How to Prevent Cyber-Attacks on Your Automotive eCommerce Website: 8 Top Threats & Hot Tips
Do you know what a hacker’s favorite time of the year is? Phishing season (if you pardon the pun)! Speaking earnestly, your eCommerce security is no joke. By our estimates, for every fraudulent order placed using your eCommerce website, you need to generate eight (!) legitimate sales to recover financially from the chargeback and lost inventory.
Along with fake orders, online entrepreneurs may deal with security breaches jeopardizing their business data integrity. To make matters worse, it also comes with a hefty price tag, averaging 4.24 million dollars, and counting.
Apart from sales profit loss, companies may face far more detrimental cybercrime consequences that include:
- data damage or destruction
- identity theft
- post-attack disruption of sales cycle
- cost of recovery after a data breach
- reputational harm
- the list goes on
Given that no eCommerce site is immune to the growing number of cyberattacks and data breaches, online sellers have to approach security proactively.
In this guide, we explore common digital commerce security threats, uncover appropriate fraud protection tools, and provide up-to-date tips on ensuring your online store’s security.
So, let me fill you in one step at a time.
I. The Basics of eCommerce Business Security
Driven by the surge in online sales during COVID-related lockdowns, the activity of cybercriminals has increased by 75% compared to the pre-pandemic levels. This spike gave rise to a number of eCommerce security threats and challenges that online sellers have to face.
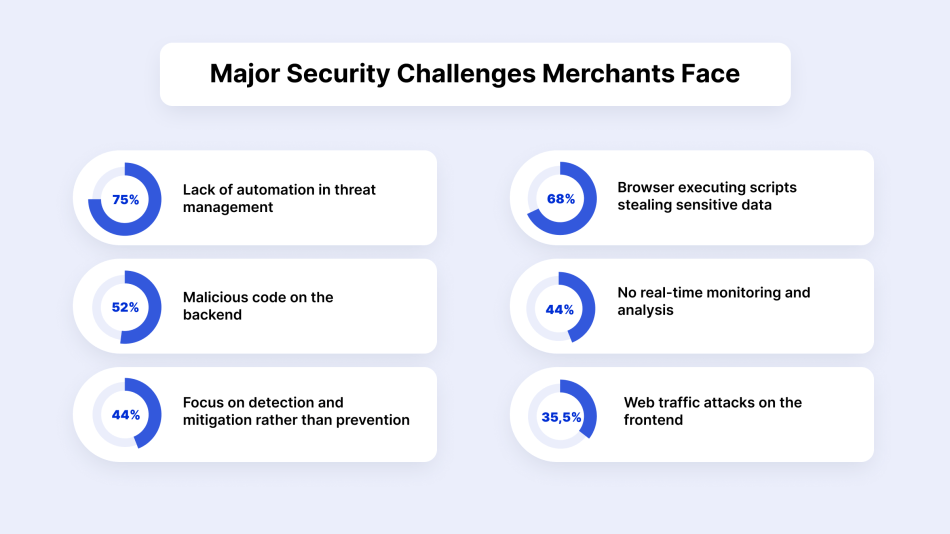
We’ve put together a list of six pillars that influence your overall eCommerce security:
- Multi-factor authentication (MFA) ensures that sellers and buyers present their identity verification to guarantee transaction safety.
- Integrity maintains the information’s consistency and accuracy, and assures that stored data has not been modified without authorization.
- Privacy refers to protecting customers’ sensitive data and blocking unauthorized access.
- Non-repudiation confirms that both buyers and sellers received the information sent from each other. In other words, buyers can’t deny the legitimacy of a recorded transaction.
- Availability of the eCommerce website increases online visibility, search engine rankings, and site traffic. It assures that access to the eCommerce shop’s data is timely, available, reliable, and restricted to authorized users.
- Compliance sticks with numerous industry regulations and standards that eCommerce businesses should follow to minimize security risks and avoid penalties for non-compliance.
eCommerce Security & Compliance
Your eCommerce store represents a complex system where multiple components have to interact with each other — your server, web apps, users, and network connection. All of them should be protected from any forms of threats, malicious attacks, data theft, and financial fraud. To make the business security system function without a hitch, one should implement multiple security monitoring tools and software that conform to international compliance standards.
Side note: Although the concepts of compliance and cybersecurity go hand in hand, they are not interchangeable.
eCommerce security refers to various activities and measures that protect your website from threats and keep your online transactions safe.
eCommerce compliance is the ability to meet specific standards and industry regulations set out by governments or private institutions to minimize security risks.
As an auto parts online store owner, you must meet one or more of these compliance standards:
- PCI DSS (Payment Card Industry Data Security Standard) ensures the secure storage of credit card data and the encrypted transmission of that data across public networks.
- SOC (Service Organization Control) reports display how the company manages financial or personal information and protects it from unauthorized access.
- ISO/IEC 27001 (International Organization for Standardization) is one of the standards defining the requirements for information security management systems.
- GDPR (General Data Protection Regulation) protects and controls how European customers’ data is collected, processed, or sold.
- CCPA (California Consumer Privacy Act) focuses on consumer data protection rights within California. For online merchants selling their products to consumers in that state, compliance with these regulations is a must.
- FMVSS (Federal Motor Vehicle Safety Standards) are mandatory U.S. safety regulations that set minimum performance requirements for motor vehicles and their safety-related components.
- EPA Emissions Standards (Environmental Protection Agency) are federal regulations prohibiting the sale of parts that alter or bypass a vehicle’s emissions control system.
- CARB (California Air Resources Board) regulations are state-specific emissions standards that must be met for products sold to consumers in California.
- ACES & PIES (Aftermarket Catalog Exchange and Product Information Exchange Standards) are data standards for the North American automotive aftermarket that help ensure accurate product descriptions and fitment information.
Even if you regularly perform security checks, ensure compliance, and take care of customers’ sensitive data, you should never relax. Online fraud evolves rapidly, and online sellers should do their due diligence in keeping pace with the latest cyber threats.
8 Most Significant and Common eCommerce Security Threats
Given the variety of online security threats, we have chosen to focus on the most prevalent types of cyber attacks and, most importantly, what you should do to prevent them from happening.

1. eCommerce Fraud
Financial cyber attacks include any deception conducted during a transaction for financial or personal gain. For online sellers, fraudulent transactions entail the risk of significant profit losses. According to Statista, eCommerce losses to online payment fraud were estimated at 20 billion U.S. dollars globally in 2021.
The most common types of eCommerce fraud are:
- Credit card frauds due to stolen credit card data
- Unauthorized transactions through account takeover
- Fake returns & refunds by initiating a fraudulent chargeback or disputing a legitimate transaction
What Are the Warning Signs of Fraudulent Transactions?
- More than one payment method is being utilized from a single IP address. This could be an individual using stolen credit card numbers to submit orders and receive goods they can sell.
- Billing and shipping addresses don’t match. Most software can only verify addresses properly within the US and UK.
- Large volume orders on a single item coming from a new customer. This could be a cybercriminal acquiring a product to resell with someone else’s credit card.
- A series of orders is shipped to the same address but placed using different payment methods.
Expert Tips:
- Monitor your online transactions and configure system alerts for any suspicious activity or fraud.

Signifyd provides a 100 percent financial guarantee against fraud and chargebacks on every approved order. The guarantee shifts fraud liability away from online sellers and lets them focus on increasing sales, opening new markets, and building their brands.
Side note: At X-Cart, Signifyd is available via the X-Payments Cloud connector.
- Don’t store customers’ payment credentials on your eCommerce website or utilize a certified data encryption service.
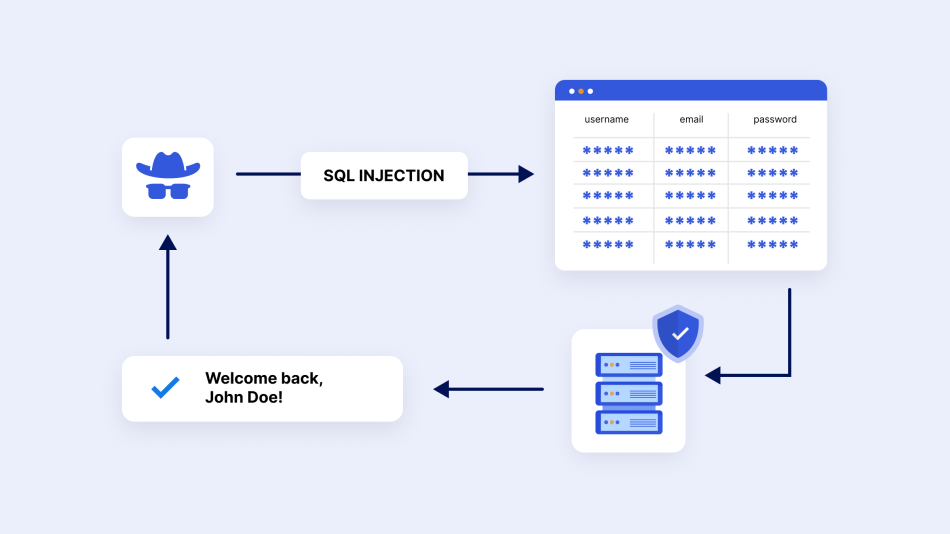
2. Cyber Threats through SQL Injection
SQL injection, also known as SQLI, is a type of attack that uses malicious SQL code to manipulate backend databases and access sensitive information.
For example, how your customers sign up for an email newsletter or set up an initial consultation.
Expert Tips:
- Scan your website to block hackers and keep your online activity private. Internet security companies, like Norton, have products to help you detect and patch vulnerabilities. But, you can also find free site scanners such as Qualys FreeScan or Grabber.
- Web Application Firewall (WAF) is a security solution that checks traffic coming to your server and takes necessary action to protect it from hackers and malware.
Side note: This security tool also protects your website from common vulnerabilities like Cross-Site Scripting, DDoS, and Brute Force attacks.
3. Cross-Site Scripting (XSS)
During this kind of cyber attack, bad actors perform a purchase by typing a malicious script into an order form on the target eCommerce site. The embedded “data-stealing JavaScript” hooks a user’s mouse clicks on the website during the login attempt or during the transaction.
As a result, it steals the customer’s username and password or credit card information.
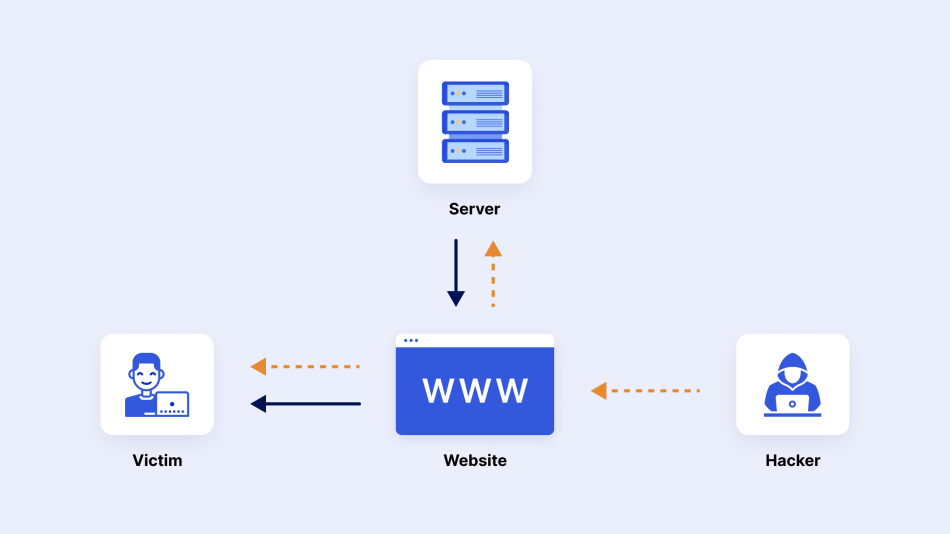
Even though this attack doesn’t impact your eCommerce shop itself, it exposes your shoppers’ credentials to phishing attempts. Therefore, admins should block fraudulent server requests that can compromise your online store’s security.
Expert Tips:
- Ensure that your shopping cart solution is up-to-date. Reputable eCommerce platforms and third-party tools provide ongoing updates based on common security threats.
- Automated fraud detection solutions to timely roll back a fraudulent change to your core data with a click of a button.

OSSEC is a free, user-friendly tool for real-time analytics of your system security events and server uptime monitoring. If a hacker manages to make malicious changes, you’ll be immediately alerted to quickly notify the customers about the temporary problem and proceed with the investigation.
For X-Cart customers: Update your software regularly. Automatic updates should be standard practice to add new features to the store, update existing ones, and prevent new vulnerabilities to viruses and malware.
To protect their X-Cart stores from XSS attacks, merchants can also configure the etc/config.php file to return special headers.
For this purpose, they should find the following parts of code in the etc/config.php file and set the appropriate value depending on the case.
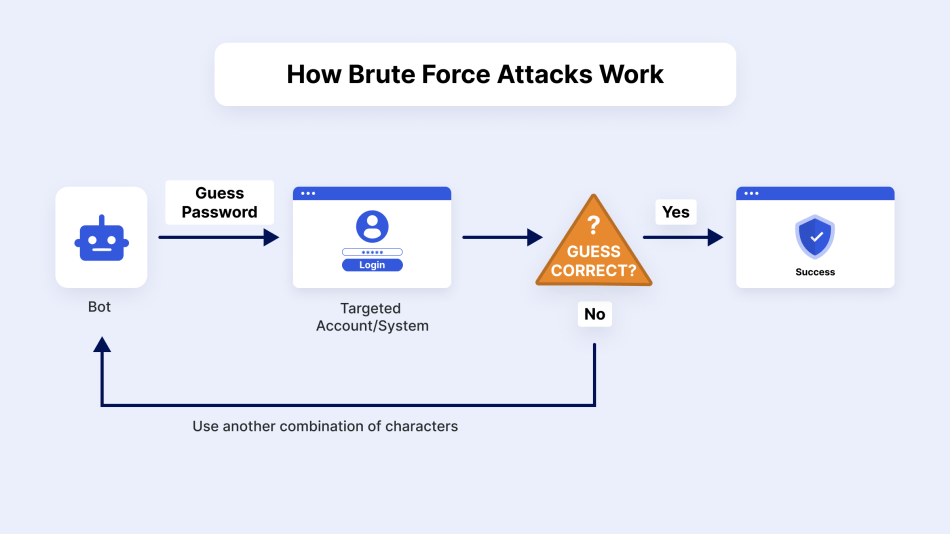
4. Brute Force Attacks
Simply put, they are automated attacks that use trial-and-error to guess possible passwords or passphrases to gain access. Typically, they target admin panels and consumer accounts.
Expert Tips:
- Require multi-factor authentication before users can log in.

Two-factor authentication is a free app on the X-Cart App Store that requires shoppers to supply a 1-time passcode in addition to their login details.
- Utilize a captcha or a similar tool to challenge visitors to your login page.
- Use complex and lengthy passwords featuring symbols, capitalization, and numbers.
X-Cart has a special built-in Brute Force protection for both admin and customer logins. For example, in case of six failed login attempts (wrong password for a username), the login form is automatically blocked for two minutes.
Each failed attempt to log in with the admin’s email address is registered, and the admin gets an email notification about an account takeover attack.
5. DoS & DDoS Attacks
Both malicious actions have the same goal: to shut your eCommerce site down and make some profit from that. But technically, they are different.
A DoS (Denial of Service) attack is an attempt to shut down your online store, flooding it with junk traffic and making it unreachable to regular users.
A DDoS (Distributed DoS Attack) attack is performed from multiple devices or a botnet (AKA ‘gang’ of computers infected with some malware).
In essence, your server receives a flood of requests from many untraceable IP addresses, causing it to crash and making your online store unavailable to visitors.
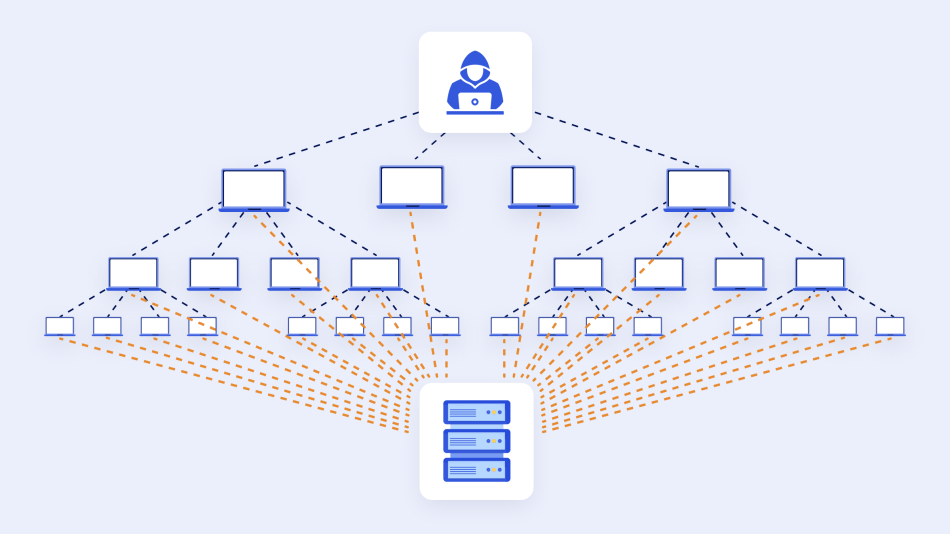
The cost of a DDoS attack for online sellers averages between $20,000-$40,000 per hour.
Expert Tips:
- Implement a rate-limiting feature to protect your website from malicious requests.
- Monitor network traffic.
- Strengthen the eCommerce website security as a whole with a backup policy and keep your software up-to-date.
While rebuilding lost resources takes days and possibly weeks, restoring from a backup takes nothing but a few mouse clicks.
For X-Cart users: Our eCommerce platform performs automated daily backups in the background.

Backup Master will create a SQL dump file of your website database and include it in the backup file. It can also be useful when upgrading your store from one version to another, saving all the valuable information.
For online stores using secure VPS hosting, backups are created automatically and on a regular basis.
While most VPS providers don’t back up user’s data, we keep an up-to-date copy of the merchant’s website and store two backup copies in geographically different locations outside the location of the user’s virtual environment.
Thus, the entire configuration of the user’s environment can be easily and quickly reproduced in case of a data breach or if data needs to be transferred to another location.
6. E-skimming
E-skimming, also known as a Magecart attack, is a hacking technique for stealing credit card and personal data from payment card processing pages. Attackers gain access to an online store via a hidden malicious code to capture payment information that shoppers enter on the checkout page.
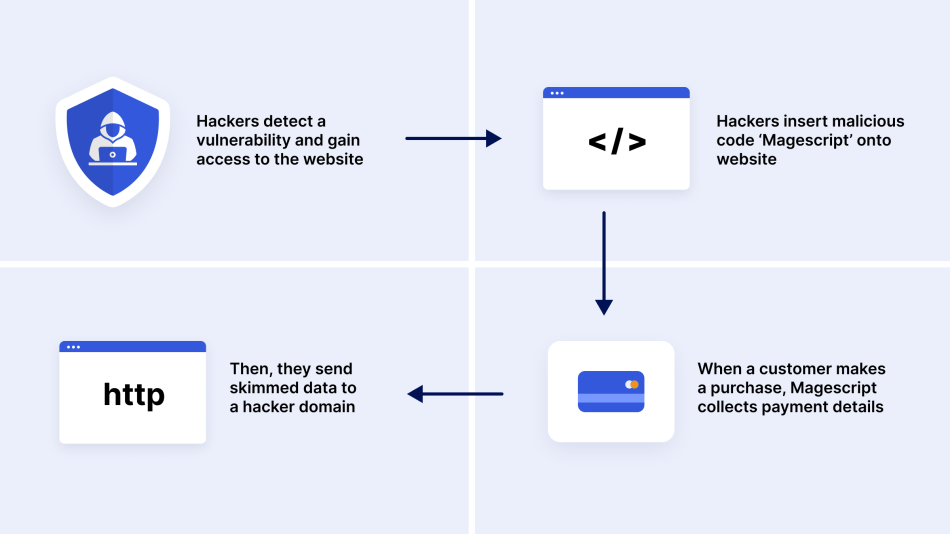
Expert Tips:
- PCI DSS compliance, AKA Payment Card Industry Data Security Standard, is dedicated to decreasing credit card theft and fraud. Even if your store is compromised, credit card details are safe, as you don’t store them on your website.
Side note: X-Cart shopping cart solution doesn’t store your customers’ financial data. Instead, it offers a bunch of PCI-compliant third-party payment gateways that can securely handle customer financial data on your behalf.
Here are the five most popular payment solutions that X-Cart store owners use:
- PayPal uses the latest technologies to seamlessly streamline transactions and help secure card data by redirecting shoppers from your online store to the payment gateway site to enter credit card data.
- X-Payments Cloud Connector is a PCI Level 1 certified payment solution that will allow you to store credit card data right on your website and still be compliant.
- Stripe can assign risk scores to every payment and automatically block high-risk payments. Furthermore, Stripe algorithms adapt quickly to shifting fraud patterns and to your unique business.
- Skrill provides high-security standards and anti-fraud technology to offer sellers a convenient and secure way to receive online payments in their stores.
- With Authorize.Net SIM, shoppers complete the payment on the side of Authorize.Net, which means that you can use a shortened PCI Self-Assessment Questionnaire during the PCI DSS compliance assessment of your eCommerce Website.
- Identity theft detection

With NoFraud built in and enabled in your platform, you will forget that phishers exist. This sophisticated solution, based on the fusion of machine learning and human intelligence, reduces fraud to below 0.01%.

Kount fraud prevention service delivers accurate and scalable protection to maximize sales opportunities. According to Kount, one of the aftermarket parts industry leaders confirmed that their bottom-line sales grew by an average of 2.2% – 5.8% after its implementation.
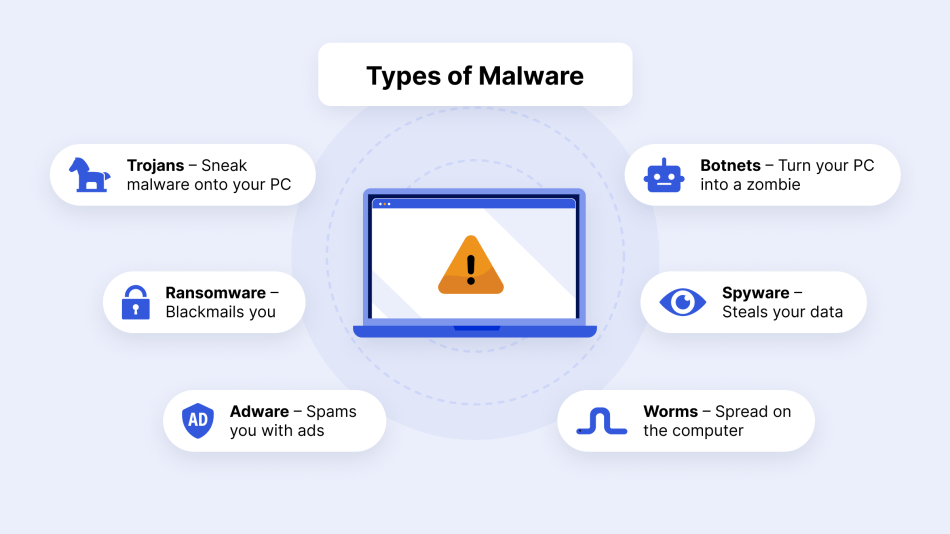
7. Malware Data Breaches
Malware is designed to steal data, send spam from your domain, or provide lateral activity to find a way to other areas of your data via remote access tools. These malicious programs include ransomware, spyware, adware, trojans, bots, and worms.
According to Business.com, 43% of all data breaches, including malware and ransomware attacks, happen to small businesses. They also reported that 60% of the small companies hit by a cyberattack went out of business within six months after the incident.
The following are the main consequences of a malware attack:
- Malware issues can open websites up to fines and lawsuits.
- Bad online reviews related to security concerns can hurt sales.
- Google can remove websites from search engine result pages.
That said, online sellers should be on the alert to take relevant security measures, as data breaches come at a high cost for any business, regardless of size.
Expert Tips:
- Make sure you do regular backups of your website data and have malware detection and removal tools implemented.
Short Hint: Implementing automatic malware removal tools to catch and eradicate problems before any significant damage is done can help you protect your store from being compromised and recover a hacked website using a variety of tactics:
- configuring automated backups of the software and database
- checking third-party applications, add-ons, and modules for possible security issues
- 24/7 website content check, core files integrity, and server monitoring
- cleaning up the code and database from malicious insertions.
Don’t Wait Till Attack Occurs
8. Social Engineering
It is a type of cyber fraud in which a hacker pretends to be a genuine contact. This can take the form of an email from a business partner or a phone call from a customer, which is why these fraudulent communications can be hard to spot.
Phishing is a social engineering technique that replicates a real web server or application to distribute harmful attachments and steal users’ credentials. According to the ITGovernance report, 14.6 % of all phishing attacks target the eCommerce industry.
At the same time, SOCRadar detected almost ten thousand phishing domains impersonating retail eCommerce sites like Amazon.com in 2021.
Expert Tips:
- Monitor your website and email data for suspicious attachments, poor message formatting, bland email greetings, and phony email addresses.
- Secure your web browser and operating system. According to Blokt, Google Chrome and Safari present several privacy issues, making it hard to recommend them as secure browsers. Instead, you can use Firefox Quantum or Brave, which come with several built-in privacy and security features.
- Encrypt all sensitive company information. To secure the information sent between your website and your customer’s computer, you need to use data encryption. And this is where a Secure Socket Layer (SSL) certificate makes the case.
Side note: An SSL certificate is a small data file installed on a web server that allows for a secure connection between the server and a web browser.
SSL certificates secure all sensitive data transfers, such as credit card transactions, logins, and other personal data passed from your customers’ browsers to your online store.
In sum:
To stand against hackers, you should approach your digital security holistically.
| eCommerce Security Basics | X-Cart and Services offered by X-Cart team |
| Credible eCommerce platform | ✔ |
| Secure Web Hosting | ✔ |
| HTTPS security protocol | ✔ |
| PCI PSS Compliance | ✔ |
| An SSL Certificate | ✔ |
| Reliable and PCI-compliant payment solutions | ✔ |
| Regular software updates and backups | ✔ |
| Easily integrable fraud prevention solutions | ✔ |
| An in-house team of professionals providing hack repair services | ✔ |
Any website can be a hacker’s target, but if you take precautions, you can avoid getting affected by malicious users. With a shopping cart solution that ticks all the boxes mentioned above, you can take your business security to the next level, reduce the number of hacker attacks, and regain your customer loyalty.
And, the X-Cart eCommerce platform is one such solution.
FAQ
Is my eCommerce website secure?
To understand this, perform regular security audits to spot and patch vulnerabilities. The frequency depends on the size of the organization and the type of confidential/sensitive data the company is leveraging. We recommend doing audits at least twice a year.
2. Open-source vs. closed-source software: which is secure?
Closed-source software makes it easier for the company to control the development environment. Yet, this doesn’t necessarily mean that closed-source code is always safer; it simply comes down to the quality of the developers.
In contrast, open-source code is created by an open community of developers, meaning that the code is more transparent for potential vulnerabilities.
3. What is an eCommerce Security Badge?
This trust badge helps to demonstrate the legitimacy of the eCommerce website. Thus, a “Guaranteed Safe Checkout” badge denotes that an SSL is used during checkout.
Some eCommerce websites that use vetted third-party service providers may also add a “Money back guarantee” badge or other service-related badges.
4. What are the 5 dimensions of e-Commerce security?
The five dimensions are:
- Integrity: Protection against data alteration. It keeps information accurate and tamper-free.
- Confidentiality: Protection against unauthorized data view. Only authorized people can see sensitive information.
- Privacy: It lets customers control the personal information they give to an online business.
- Availability: The ability for a website to operate and be accessible to legitimate customers when they want to shop.
- Authenticity: The ability to verify who is interacting with the website, both a user and a business.
What is an example of a security tool used in eCommerce?
A secure payment gateway is a key example. It helps protect transactions by using a decryption key to process card data safely. A gateway also supports proactive security measures, such as access management, to control who can see critical systems.
Many eCommerce businesses use these tools to protect customer data. A secure gateway is often a third-party service that helps your online business combat things like malicious software and helps protect transactions.
Wrapping Up
For all-sized businesses, the cost of a breach in loss of data and customer confidence can be detrimental. Therefore, we’re closing the article with a straightforward 5-step plan to help you get ahead of cybercrimes:
- Evaluate the security vulnerabilities of your business and the economic value of a data breach.
- Create a cybersecurity strategy that would cover your business’s complete ecosystem – customers, partners, vendors, and employees.
- Implement automated, comprehensive cybersecurity solutions that offer complete visibility into infrastructure, traffic, and assets.
- Stay ahead of rapidly evolving malicious techniques to curb them before they deal a crippling blow to your eCommerce business.
- Let the team of professionals do the heavy lifting of enforcing preventative measures against cyber threats on your behalf.
About the author