The Detailed Guide to WordPress Vulnerabilities and Exploits [+ How to Fix Them]
This blog post was originally contributed by Gary Stevens, a blogger at Hosting Canada.
Since the early days of the internet, WordPress has served as one of the most reliable content platforms available to individuals and organizations. Whether being used for a personal blog or a corporate homepage, WordPress is a flexible and robust content management system (CMS).
However, like any piece of software that integrates with the open internet, WordPress is susceptible to attacks and viruses. And because of the number of people using WordPress on a regular basis, hackers are looking more and more for potential vulnerabilities. So how do you protect yourself, your organization, and your data?
Read on to learn about some of the most common WordPress vulnerabilities and how to combat them effectively.
1. Database Injections
All WordPress installations rely on a SQL-based database backend for storing critical information and records. In general, direct access to the database should be extremely limited, and all updates should be routed through the web application. But even that is not enough to secure yourself from outside attacks.
An SQL injection is a very common form of cyberattack because it can be initiated with minimal action. Hackers will usually take advantage of an input field on a WordPress webpage and use it to run a database query that will either look up information or delete records entirely.
SQL injections are dangerous because they could result in a significant data breach from your WordPress database, including private user data or even usernames and passwords. Hackers can also use SQL injection to corrupt your database and bring down the entire WordPress environment.
If you manage your WordPress code directly, then you can reduce the risk of SQL injection attacks by parsing all input strings to look for dangerous command words or symbols.
Otherwise, the best course of action is to keep your WordPress theme up to date and to run a security scan on a regular basis.
2. Cross-Site Scripting
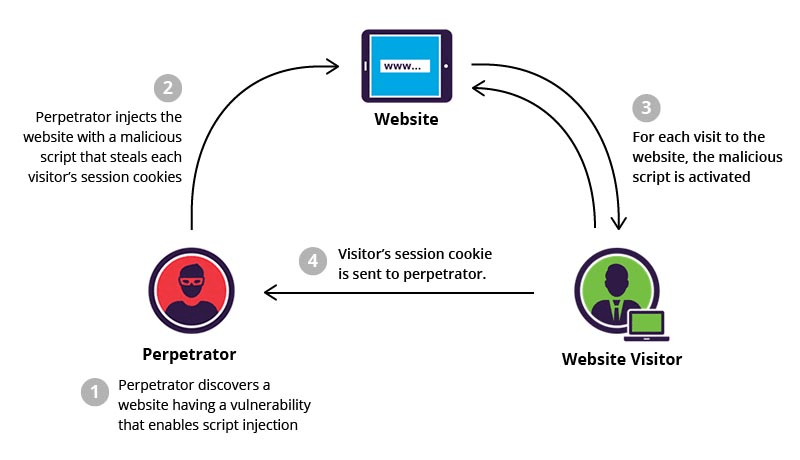
In some cases, a hacker will target the users of your WordPress site rather than the code or database that sits behind it. The most common form of this is a cross-site scripting (XSS) attack, which is commonly found in blog templates or other themes where user comments are allowed.
During an XSS attack, the hacker will post dangerous content to your WordPress site that contains JavaScript code to execute each time another user loads the page. When this happens, the user may see an unusual pop-up or be redirected to an outside URL.
XSS attacks are often run like email phishing scams, with the goal of having users navigate to their nefarious webpage and either enter their WordPress password or some other identifying information. In the worst-case scenario, financial data can be stolen and used to forge an identity.
As a WordPress developer or site admin, you should use sanitizing scripts on any portion of your code that receive external data from users. These scripts will check for dangerous JavaScript code and block it from executing on the live system.
3. WordPress Plugin Vulnerabilities
The core WordPress codebase includes a wide range of features and tools, but when you want to expand what’s possible on your eCommerce site, the place to look is the third-party plugin community. Thousands of developers create and maintain special add-ons for tools like email management, eCommerce support, or analytics tracking.
First of all, whenever you are considering adding a new plugin to your WordPress environment, make sure you are downloading it from a reputable source and developer. If you can’t verify that the source is trustworthy, then it is too risky to add the code to your eCommerce website.
Hackers will often hide malware or other dangerous scripts within plugins that claim to be performing a harmless task. If you get suspicious that there could be a plugin causing issues in your online store, immediately disable them all through the admin console and add them back one by one to identify the root cause.
Occasionally, a security vulnerability will be found within a specific plugin, and the developer will work to provide a patch. You must install these types of security updates manually through the admin console. Check for updates on a regular basis so that your site is not at risk.
4. Malware From Attachments
Many WordPress sites are required to support file upload and storage. For example, users might want to add text documents or graphic files to a folder and then share that content across their organization or team. WordPress code can handle that activity and manage file storage on backend servers.
But by making your WordPress environment open to file uploads, you increase the risk that dangerous data could be injected onto your server side. Hackers will try to mask a virus in common file types and then have them execute once they are stored within WordPress.
The biggest risk is that a piece of malware from a rogue attachment could potentially grant hackers full access to your WordPress environment as an administrator. That could lead to a significant data breach or extended downtime and data loss for your entire site.
To protect against malware attacks, you should scan for dangerous files at both the WordPress and operating system levels. Make sure you invest in a reputable scanning tool or security plugin that is set to run on a regular basis. Also, remember that virus scanners need to be refreshed daily to capture new definition files.
5. Cloud Host Security
When securing your WordPress environment, you have to keep in mind that your code and database are always residing on physical hardware. The security of that infrastructure is directly tied to your site’s health and performance, so it’s critical to tightly manage your hosting approach.
Hosting WordPress sites in the cloud is the most common approach these days, although that does introduce risk as you are forced to trust the provider that will be maintaining the required hardware. If you are experiencing performance or security issues with WordPress, you should seriously consider migrating to a new cloud host.
Make sure to research a wide range of web hosting companies, focusing on ones that have experience with WordPress environments. Try to avoid using cost as your only decision making factor, as it can lead you to a provider that is, shall we say, less than dedicated at keeping security vulnerabilities out of its underlying infrastructure.
6. Cookie Hijacking
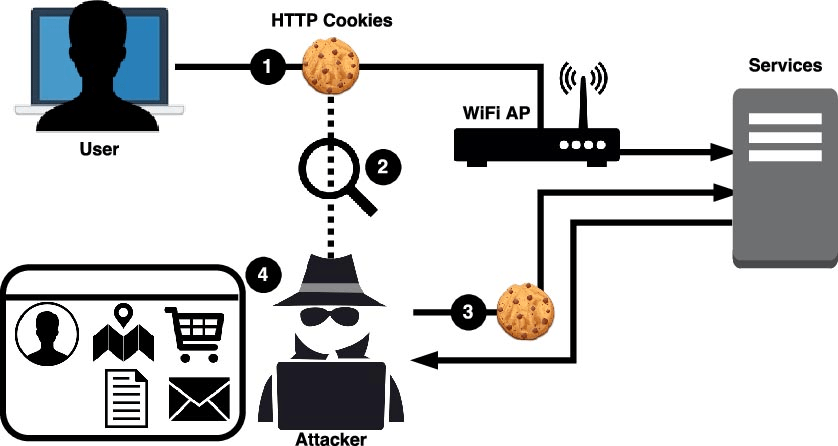
Cookies are used by almost every website that you visit on the internet. They are small text files that are stored within your web browser’s memory in order to track your identity and activity within a site. For example, this is how you can stay logged in to certain websites even after closing your browser.
WordPress supports cookie integration for blog templates, plugins and themes. The cookies track user sessions while they are logged in to the WordPress platform and are adding content or comments. Cookies are meant to be unique to the active user an anonymous to everyone else.
Hackers have developed methods to intercept cookies during active web sessions as part of larger cyberattacks. When that happens, they are able to steal authentication credentials and access the WordPress site as if they were logged in as a valid user.
To reduce the risk of attacks, consider adding SSL encryption to your site’s cookie transmission. This can be accomplished through a PHP script or a special plugin.
7. Email Utilities
All basic WordPress installations come with the PHPMailer tool built into the codebase. This allows you to integrate automatic email sending with your blog, website, or eCommerce store. For example, you may want to generate a new message every time a purchase is made by a customer.
Recently there was a dangerous vulnerability found within PHPMailer that could cause significant issues for backend systems. The issue is classified as a remote code execution (RCE), which allows for a hacker to run administrative commands without the appropriate level of access.
The bug in the PHPMailer tool can allow for attackers to insert shell commands within an email address text field and then have the commands run directly on the WordPress host. This could result in administrators losing control of the WordPress environment and potentially losing a large amount of data.
WordPress has included a patch for the PHPMailer bug within a recent security update. You can find these updates in the admin console and even set your environment to install them automatically.
8. Backup Integrity
It’s smart to keep regular backups of your WordPress code and database, especially if you are using a cloud hosting provider and do not have direct access to the hardware. Many plugins are available that will copy the WordPress data and store it on a separate instance or server.
When selecting a backup utility plugin to use, make sure it is one that transfers data over an encrypted SSL connection. Otherwise, there is a chance that hackers could intercept the information in transit and uncover the directory structure of your WordPress codebase.
With the directory structure information, a hacker could potentially infiltrate the repository of your backup history and be able to browse through earlier copies of your site data. These database copies may contain sensitive customer information, especially if you are running an eCommerce website through WordPress.
9. Firewall Gaps
A firewall can be either a software tool or a physical device. In both cases, the firewall is designed to filter all incoming traffic and determine whether it should be allowed through or blocked. Many organizations use firewalls as a virus protection layer for reducing hacking threats.
From a WordPress perspective, you will find a number of third-party plugins that claim to add additional security protections to your code and data. You should be wary of these tools unless they come from a reputable security company that has been vetted by technical professionals.
Some WordPress firewall plugins have been found to mishandle their logging records that could allow hackers to intercept information or bypass the security blocks. Until your firewall plugin has patched this vulnerability, you should disable it through the admin console or remove it entirely.
10. Admin Console Security
The admin console within WordPress acts as a portal for all common functions that you need to use for managing a blog or website. For example, you can change the theme template of your site or control which users have the ability to add new content to a blog.
As a rule, you should limit access to the admin console to only the individuals who absolutely require it. Otherwise, you risk that a password could be intercepted or stolen and then used by a hacker. From the admin console, an attacker would be able to take down a site or hijack it for phishing purposes. This could put all of your WordPress users in danger and potentially lead to a data breach.
Within the admin console, you can set up constraints to make sure that all users have complex passwords that are changed on a regular basis. To add more security, consider implementing multi-factor authentication to require users to input a text message code each time they attempt to log in to the admin console. This lowers the risk that an intruder could steal login credentials.
Conclusion
The WordPress software community is constantly evolving, and that means, as a system administrator, you need to stay up to date with the latest security threats and the best remediation methods.
Think like a hacker and remember that they are always looking to stay one step ahead of security tools.
Due to the massive size of the WordPress community, it will remain a constant target for cybercriminals and other forms of digital attacks.
To be as safe as possible, you may want to consider hiring an outside technical consultant to run penetration tests and find potential vulnerabilities before a real hacker can take advantage of them.
About the author